Artificial intelligence (AI) is transforming the world of finance, with numerous applications in areas such as fraud detection, credit assessment,
Continue reading
Uid=0(chris) guid=0(security specialist) groups=1(Advisor), 2(Security) 3(Privacy), 4(Architect), 5(Business), 6(Human)

Artificial intelligence (AI) is transforming the world of finance, with numerous applications in areas such as fraud detection, credit assessment,
Continue reading
Security has three areas that are very closely linked, that all bring value to any product, and are very rarely
Continue reading
Quite a lot really, I know that’s not how the song goes but, HTTPS, the common abbreviation for Hyper Text
Continue reading
This should be obvious, but on the surface, to reasonable people, this seems reasonable. If bad people are doing bad
Continue reading
Recently the development teams here have been improving their coding skills by taking on the challenge of Clean code, a
Continue reading
I have recently been listening to a few of the NDC talks from around the world and the one today
Continue reading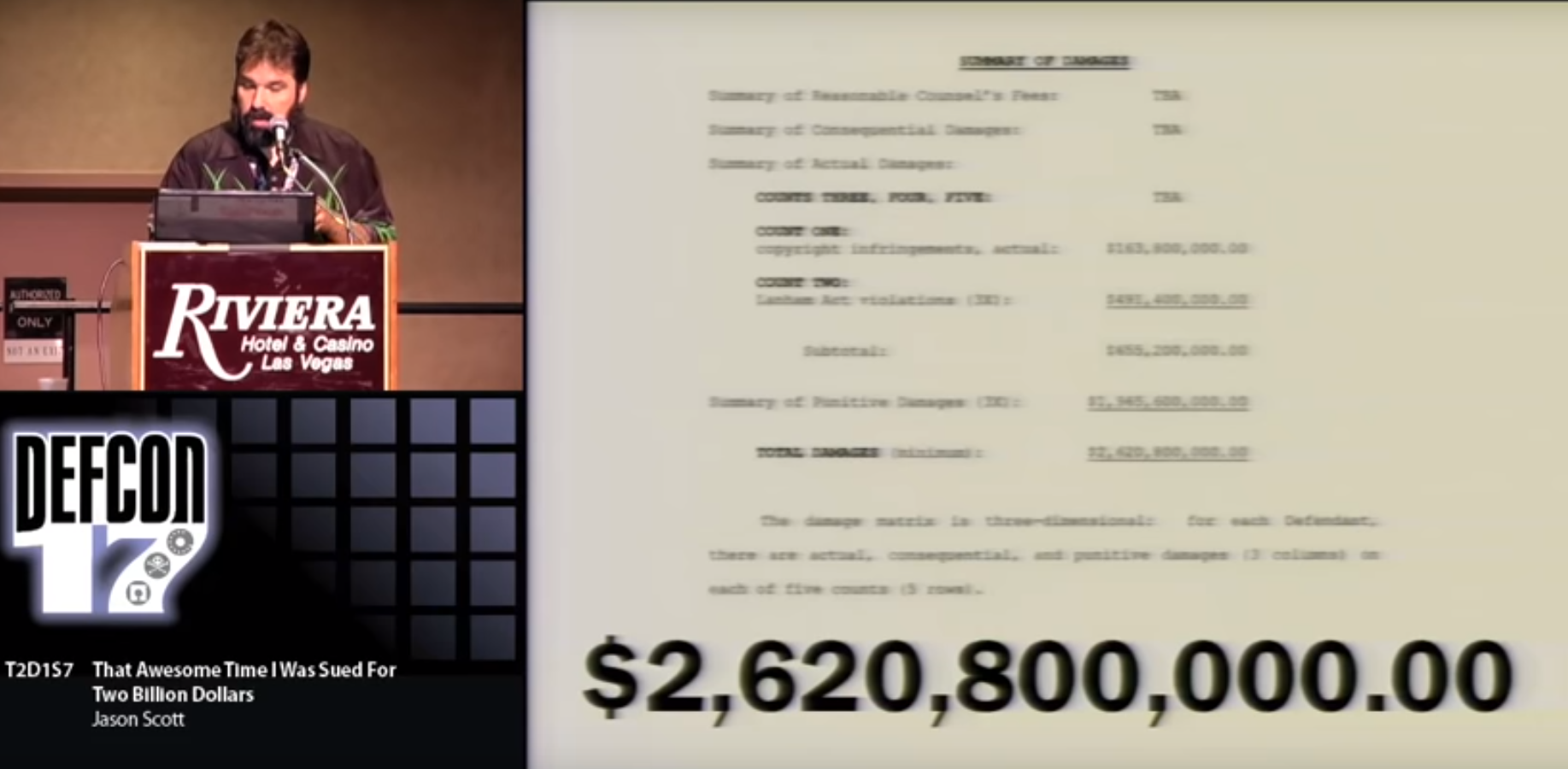
Well not me but, this is an amazing story from Jason Scott who runs Textfiles.com about a time he was
Continue reading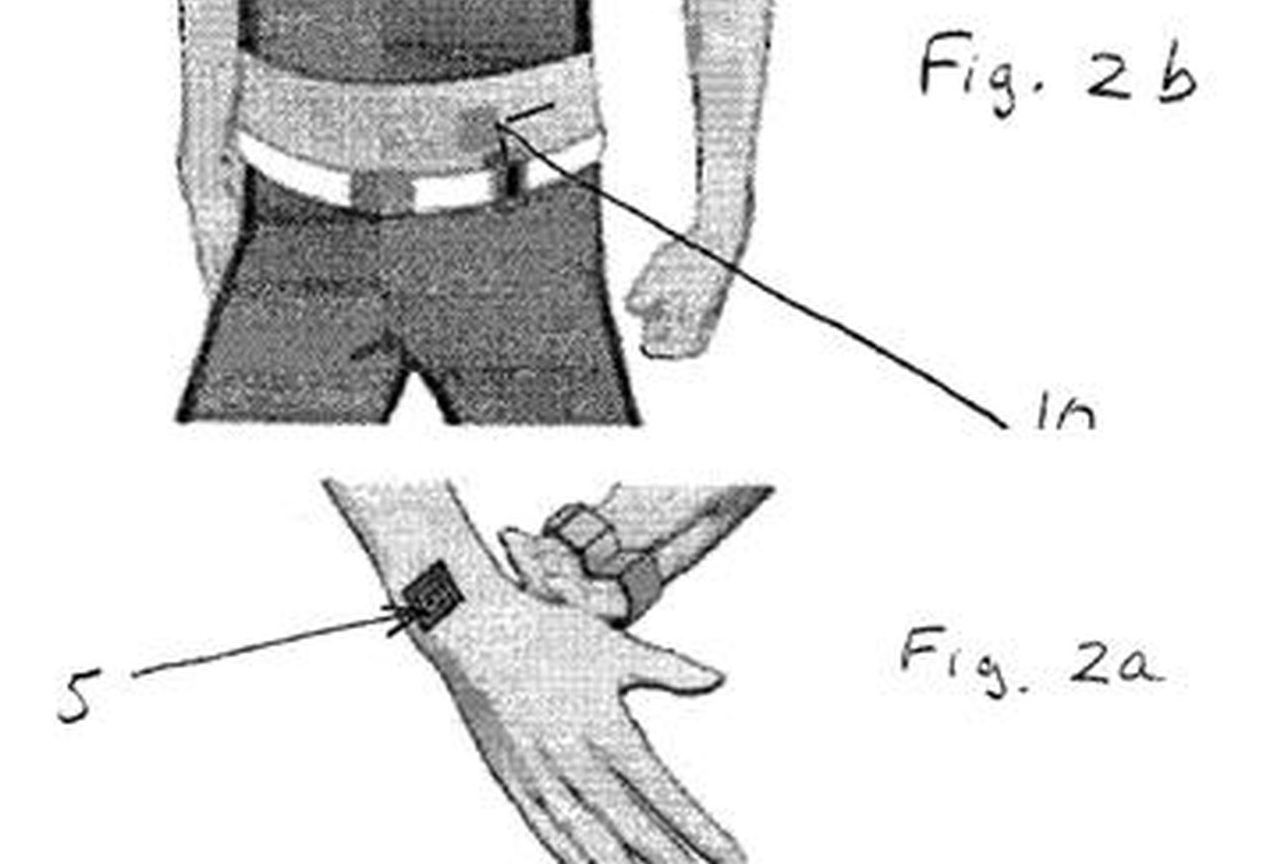
Registered on the 15th of March this year, Nokia, the world famous phone maker filed a patient for Haptic Communication.
Continue reading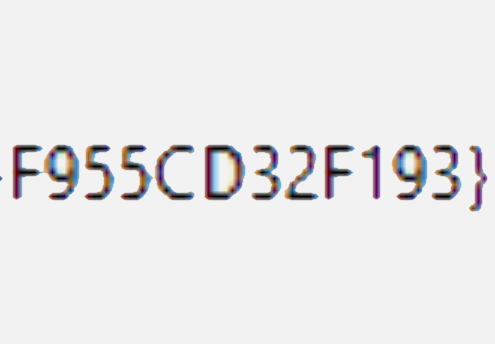
I have a have been puzzling over a problem where I need to create one-time keys to access a system.
Continue reading
I came across this article today Dodgy Coder – Coding tricks of game developers. Some of the things mentioned are genius
Continue reading