Security has three areas that are very closely linked, that all bring value to any product, and are very rarely
Continue reading
Uid=0(chris) guid=0(security specialist) groups=1(Advisor), 2(Security) 3(Privacy), 4(Architect), 5(Business), 6(Human)

Security has three areas that are very closely linked, that all bring value to any product, and are very rarely
Continue reading
Quite a lot really, I know that’s not how the song goes but, HTTPS, the common abbreviation for Hyper Text
Continue reading
This should be obvious, but on the surface, to reasonable people, this seems reasonable. If bad people are doing bad
Continue reading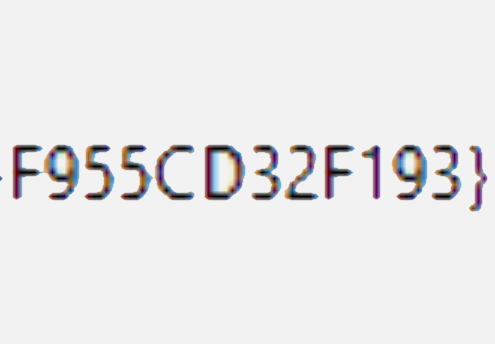
I have a have been puzzling over a problem where I need to create one-time keys to access a system.
Continue reading